The Internet
It’s time to talk about the computer, not as something isolated, but as a machine connected to many others, some in its work environment and other worldwide.
It’s been a few decades (in computer time that’s centuries for us) that the human mind began taking advantage of the information provided by a computer together with the information provided by others. That way, in the same location, we could control what was happening elsewhere, we could join several computational capabilities and we could combine various information in order to get more complete results.
This way was born the ARPAnet, which soon gave way to what we know as the Internet.
But the Internet is a computers network, thus we start there.
A computer network it’s just what its name implies: a collection of computers connected by a network, sharing resources, data and programs.
In our minds we imagine a network of wires, which until a certain degree of evolution was true, but now that network of wires must join the networks of radio, infrared, and satellite communications (WiFi, cellular network, Bluetooth, and so on).
I should mention that our goal is not to make a treaty on computer networks, but only a slight approach to the subject, allowing us to have some basics for the study of its operation, in the restricted field of Internet protocols. It will therefore be necessarily very incomplete and generic everything we write about computer networks.
We’ll mention two types of networks: LAN (Local Area Network) and WAN (Wide Area Network).
LAN is, for instance, what some of us have at home, often without realizing it. The equipment placed there in order to access the Internet and to whom we can connect multiple computers, is likely linking those computers on a local network where they can communicate with each other.
LAN is the computer network of a building, of a small or large company, of an university campus, and so on.
Any of these LAN is connected to a device with the same functions as the one we mentioned as being in our homes, which is responsible for the connection of this LAN with the world, specifically with the WAN, which in turn can connect this LAN with many other LAN or Network Servers spread around the world.
We are speaking of WAN in its broadest sense. Internet is a WAN, but a WAN is not necessarily the Internet.
The connection between two or more LAN can be performed by cable, satellite, microwave, optical fiber, and so on, through a WAN.
Let’s look at the example of a concessionary company of highways operation.
All tolls, office buildings, headquarters and others are integrated in multiple LAN. But what happens in each LAN must be of the immediate knowledge of a central management system, call it Data Center, which in turn will inform all concerned departments. The communication of the different LAN with the Data Center will be made by WAN, using dedicated lines, using public shared lines or using the own Internet.
Internet is the largest WAN, allowing the connection of any computer with information hosted on a server somewhere around the world in seconds or even milliseconds.
We don’t need to say more about what the Internet is, for surely the vast majority of those who are reading this text know as well or better than we do, what it is and does.
Our goal is to analyze how the Internet works to provide all these services, i.e., what is behind a click on a link, what happens between a click with the mouse on a piece of text in our computer and the exhibition of a page hosted in a server somewhere around the world.
For now we can say that, for this to happen, thousands of people investigated and wrote thousands of books on the methods and protocols used, which we’ll try to describe and summarize in a simple and uncomplicated manner.
Architectures of layered protocol
Before entering the discussion of this paragraph we will make some initial approaches that may help the comprehension of what we are going to talk about.
The message traffic on the Internet is done by packets, i.e., it’s packets what runs in the network. We can imagine them as the shops packets. The function of the packet is to encapsulate (isolate) the information exchanged inside it from all other traffic. Thus, the term packet that we use for the sake of better understanding, is not more than one autonomous data unit, i.e., a set of data to be read separately from the others which only makes sense if read together.
Packets, in turn, contain packets, each packet being interpreted in the context of a particular function. The smallest packet in all of these packets is the one who contains the message we want to send.
So what makes up the rest of the packets and why so many packets?
The composition of each packet is, in addition to the data of the message:
- The information needed to interpret the data,
- The information needed to ensure its delivery and delivery
order, - The needed information for its routing through the maze
that makes up the Internet or network, - The needed information for its transport along the pathways
consisting of the several hardware components that compose the
network.
We call protocol to each of these informations.
Protocol is precisely the information needed by another piece of hardware or software to understand the content of headers and data of the different packages.
And why so many packages?
To encapsulate (isolate) some information, from the one that you need to be examined, with respect to the component that is going to parse it.
This gives rise to the protocol layers.
Therefore, a layered protocol architecture is no more than a stack of layers where we put or take, as we are sending or receiving the packet, over the packet coming from last layer, the protocol that contains the information necessary to the goals we mentioned above for the layer being analyzed, just what we try to illustrate in Figure 3.
We will soon realize what each of these layers is and makes, how it is composed and what each of these components is for.
For now, as a first approach, I recommend you access the Internet and see the two films whose links I provide below. The animations are extremely well conceived and they will certainly whet your appetite to know some more. This movie was produced and imagined by Thomas Stephansom.
TCP/IP Model
In an effort to standardize the model of layers protocol architecture, the ISO (International Organization for Standardization) has implemented the OSI model (Open Systems Interconnection), which has become the reference layers model. The OSI model comprises seven layers.
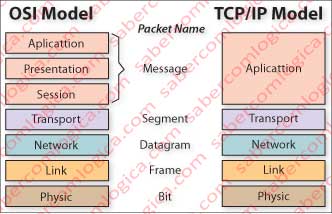
We will not comment this layers protocol, which is properly identified in the Figure 1, because this model gave rise to the simplified model used in the Internet, TCP/IP, which is the model currently used in most networks.
In Figure 1 we can see the connection between the two models with the name of the packets generated by each of the layers.
From the use of a layered architecture protocol, results that each layer provides services to the upper layer and receives services from the lower layer.
Each protocol layer in the sender of the message must match a equal layer in the receptor.
As seen in that Figure 1, the TCP/IP model consists of five layers which have very briefly the following functions;
Application Layer – It’s where the messages are prepared by the programs (applications) according to the corresponding protocol, as we shall see. The packet formed in this layer is called message and consists of the data and a header.
Transport Layer – It’s where the message transport conditions are defined, i.e., with or without guarantee of delivery, with or without delivery order, with or without detection and error correction, and so on, according to the transport protocol used. When a header is added to the message packet, a new package that will be named segment is formed.
Network Layer – The protocol introduced in this layer is responsible for addressing the message, its routing in the network and its delivery to the upper layer at the destination. The package resulting from the addition of a header to the segment is called a datagram.
Link Layer – This layer is the one where the protocol that allows the transmission of the message on the physical medium is added. The identifiers recognized by the physical equipment are different of those used until now. The resulting packet is named frame.
Physical Layer – The function of this layer is to transport the bits within the network between the equipments that will bring the packet to its destination. This form of transport varies according to the medium in which the transmission is done (copper cable, fiber optics, radio, etc.).
Just notice in Figure 2 the way headers are added to the packet in the different layers, thus forming another type of packet. The same applies in reverse order, when in each layer the corresponding packet header is removed in order to return it integral to the upper layer.
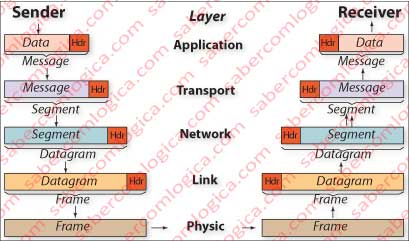
Let’s untangle a bit before proceeding. Suppose we send a letter to someone and, as we do not want anyone to know what we are saying, we agreed between us several codes that we could use to convert the text. So, after writing the message in English, we used one of the codes to convert it into illegible text, and added an Id for the used code. When he receives the message he uses the code corresponding to the Id we sent to convert the unreadable text in English. This header is the protocol, what was agreed between us to understand each other, the dictionary to translate the message. Then we placed the message in an envelope (we encapsulated it), wrote our address in the upper left corner, the destination address in the lower right corner and put in the mail.
Why did we put the sender and recipient addresses in those positions?
For thus it was agreed in the protocol used for sending mail. Through this protocol, any actor in the process knows where to read the destination and the sender addresses.
Let’s summarize this first approach.
The communication in networks is made through packets that are packaged in several layers with headers containing protocols relating to the function that each layer is intended to ensure. They are then transmitted over the physical layer and, upon arrival at destination, the packets are unwrapped, each fulfilling its function.
Well, let’s go a little deeper inside it.
